[ AWS Config ]
AWS 리소스의 변화에 대한 로깅으로 Security group 에 제한된 SSH 접근이 있는지, S3 버킷이 퍼블릭 억세스 인지, ALB(Application Load Balancer) 설정이 어떻게 변했는지 등에 대한 로깅.
region 별 서비스, 변경시 SNS 알림 가능, region/계정에 대한 집계 가능, S3 에 저장하여 Athena를 통한 분석 가능
- Helps with auditing and recording compliance of your AWS resources
- Helps record configurations and changes over time
- Questions that can be solved by AWS Config:
Is there unrestricted SSH access to my security groups?
Do my buckets have any public access?
How has my ALB configuration changed over time?
- You can receive alerts (SNS notifications) for any changes
- AWS Config is a per-region service
- Can be aggregated across regions and accounts
- Possibility of storing the configuration data into S3 (analyzed by Athena)
[ Config Rules ]
사전 정의된 룰 사용가능
각 EBS 디스크가 gp2 타입인지 확인, EC2 instance 가 t2.micro 타입인지 확인하는 등의 사용자 지정 룰 사용 가능(AWS Lambda 사용)
설정 변경시 트리거에의해 동작 혹은 스케쥴링에 의해 확인 가능.
Confg Rules 는 설정변경을 막진 않는다.
무료 아님.
- Can use AWS managed config rules (over 75 rules)
- Can make custom config rules (must be defined in AWS Lambda)
ex1: evaluate if each EBS disk is of type gp2
ex2: evaluate if each EC2 instance is t2.micro
- Rules can be evaluated/triggered For each config changes (+ at regular time intervals)
- AWS Config Rules does not prevent actions from happening (no deny)
- Pricing : no free tier, pay per configuration item recorded per region, pay per config rule evaluation per region
[ Config Rules - Remediations ]
SSM 자동화 문서를 사용하여 부적합 리소스에 대한 수정을 자동화
Lambda 함수 호출하는 사용자 지정 문서 생성 가능
자동 수정 후에도 리소스가 부적합한 경우 retry 가능
- Automate remediation of non-compliant resources using SSM Automation Documents
- Use AWS-Managed Automation Documents or create custom Automation Documents
Tip: you can create custom Automation Documents that invokes Lambda function
- You can set Remediation Retries if the resource is still non-compliant after auto-remediation
[ Config Rules - Notifications ]
- Use EventBridge to trigger notifications when AWS resources are non-compliant
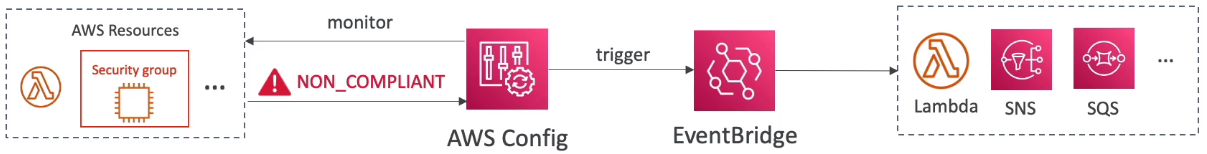
- Ability to send configuration changes and compliance state notifications to SNS (all events - use SNS Filtering or filter at client-side)

[ CloudWatch vs CloudTrail vs Config ]
CloudWatch
- Performance monitoring (metrics, CPU, network, etc..) & dashboards
- Events & Alerting
- Log Aggregation & analysis
CloudTrail
- Record API calls made within your Account by everyone
- Can define trails for specific resources
- Global Service
Config
- Record configuration changes
- Evaluate resources against compliance rules
- Get timeline of changes and compliance
[ For an Elastic Load Balancer ]
CloudWatch :
메트릭에 기반한 성능 모니터링
- Monitoring Incoming connections metric
- Visualize error codes as a % over time
- Make a dashboard to get an idea of your load balancer performance
Config :
설정 정합성 확인
- Track security group rules for the Load Balancer
- Track configuration changes for the Load Balancer
- Ensure an SSL certificate is always assigned to the Load Balancer(compliance)
CloudTrail :
어떤 사용자가 설정을 변경했는지 확인
- Track who made any changes to the Load Balancer with API calls
'infra & cloud > AWS' 카테고리의 다른 글
| [AWS] 20-1. AWS STS, Identity Federation (0) | 2022.05.24 |
|---|---|
| AWS saml (0) | 2022.05.19 |
| [AWS] 19-5. CloudTrail (0) | 2022.05.16 |
| [AWS] 19-4. AWS EventBridge (0) | 2022.05.16 |
| [AWS] 19-3. AWS Monitoring : CloudWatch Alarms (0) | 2021.09.28 |