[ AWS STS (Security Token Service) ]
AWS 리소스에 대한 임시 접근 권한 부여(임시토큰)
토큰은 최대 1시간 유효 (refresh 필요)
AssumeRole/AssumeRoleWithSAML/AssumeRoleWithWebIdentity/GetSessionToken
- Allows to grant limited and temporary access to AWS resources
- Token is valid for up to one hour (must be refreshed)
1. AssumeRole
Within your own account: for enhanced security
Cross Account Access : assume role in target account to perform actions there
2. AssumeRoleWithSAML
return credentials for users logged with SAML
3. AssumeRoleWithWebIdentity
return creds for users logged with an IDP(Identity Provider) (Facebook/Google Login..)
AWS recommends against using this, and using Cognito instead
4. GetSessionToken
for MFA(MultiFactorAthentication), from a user or AWS account root user
[ Using STS to Assume a Role ]
1. IAM Role 생성
2. IAM Role 에 대한 principal 생성
3. AWS STS 를 사용하여 자격 취득
4. 임시 자격은 15분에서 1시간 까지 유효
1. Define an IAM Role within your account or cross-account
2. Define which principals can access this IAM Role
3. Use AWS STS (Security Token Service) to retrieve credentials and impersonate(가장하다) the IAM Role you have access to (AsumeRole API)
4. Temporary credentials can be valid between 15 minutes to 1 hour
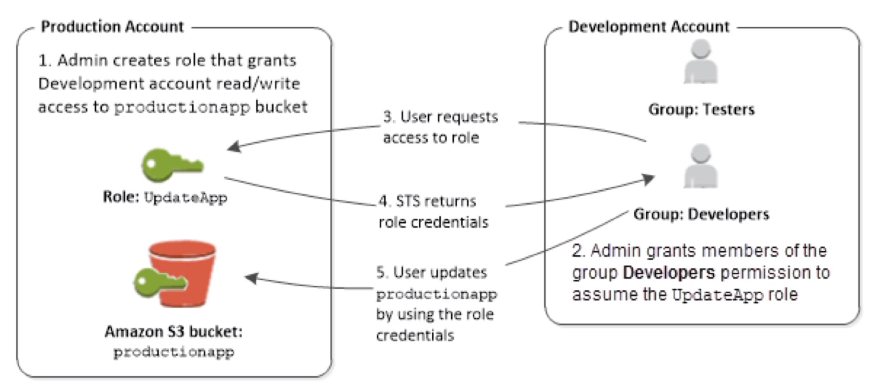
[ Identity Federation in AWS ]
Identity Federation 을 통해 외부 사용자가 AWS 자원에 대한 임시 접근 권한을 가질 수 있음
이를 사용하여 IAM 유저 생성 없이 AWS 접근 허용이 가능
- Federation lets users outside of AWS to assume temporary role for accessing AWS resources
- These users assume identity provided access role
- Federations can have many flavors
-- SAML 2.0
-- Custom Identity Broker
-- Web Identity Federation with Amazon Cognito
-- Web Identity Federation without Amazon Cognito
-- Single Sign On
-- Non-SAML with AWS Microsoft AD
- Using federation, you don't need to create IAM users (user management is outside of AWS)
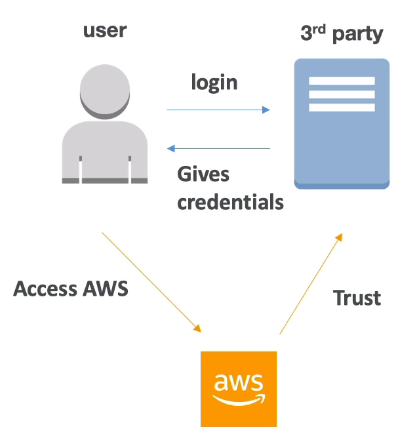
[ SAML 2.0 Federation ]
- To integrate Active Directory/ADFS with AWS (or any SAML 2.0)
- Provides access to AWS Console or CLI (through temporary creds)
- No need to create an IAM user for each of your employees
* SSO (Single Sign On) : 여러 AWS 계정 및 비지니스 앱에 대한 액세스를 중앙에서 관리 및 사용자에게 Single Sign-On 액세스 제공하여 할당된 모든 계정 및 앱을 한곳에서 액세스 가능케 하는 서비스
(AWS STS 사용하기(좌측) : https://gnidoc.tistory.com/entry/%EB%A7%A5%EC%97%90%EC%84%9C-AWS-STS-CodeCommit-%EC%82%AC%EC%9A%A9%ED%95%98%EA%B8%B0)
(SSO 사용 하기(우측 그림) : https://cloudest.tistory.com/62)
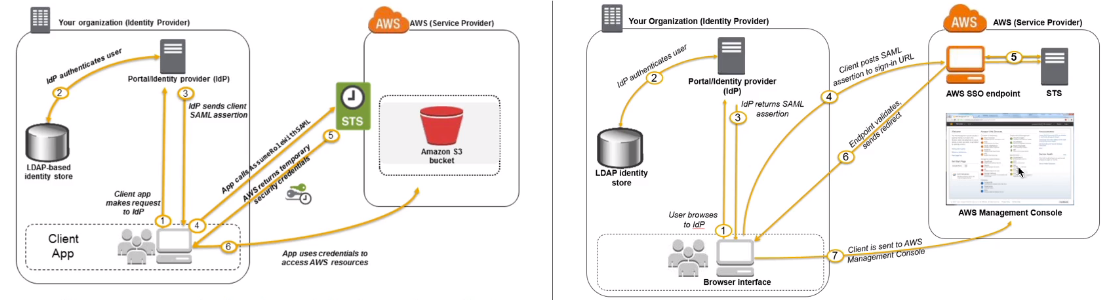
[ SAML 2.0 Federation - Active Directory FS ]
Same process as with any SAML 2.0 compatible idp

[ SAML 2.0 Federation ]
IAM 과 SAML 간의 양방향 신뢰 설정 필요
SAML2.0 은 웹기반에서만 동작
AssumeRoleWithSAML STS API 사용
가급적 SSO 사용
- Needs to setup a trust between AWS IAM and SAML (both ways)
- SAML 2.0 enables web-based, cross domain SSO
- Uses the STS API : AssumeRoleWithSAML
- Note federation through SAML is the old way of doing things
- Amazon Single Sign On(SSO) Federation is the new managed and simpler way
[ Custom Identity Broker Application ]
SAML 2.0 사용 불가할 경우 사용
AssumeRole/GetFederation 토큰 등 STS API 사용
Use only if identity provider is not compatible with SAML 2.0
The identity broker must determine the appropriate IAM policy
Uses the STS API : AssumeRole or GetFederation Token

[ Web Identity Federation - AssumeRoleWithWebIdentity ]
Not recommended by AWS - use Cognito Instead (allows for anonymous users, data synchronization, MFA)
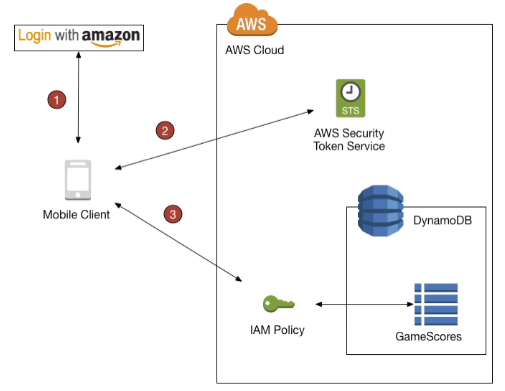
[ AWS Cognito ]
Goal :
- Provide direct access to AWS Resources from the Client Side(mobile/web app)
Example :
- provide (temporary) access to write to S3 bucket using Facebook Login
Problem :
- We don't want to create IAM users for our app users
How :
- Log in to federated identity provider - or remain anonymous
- Get temporary AWS credeantials back from the Federated Identity Pool
- These credentials come with a pre-defined IAM policy stating their permissions

'infra & cloud > AWS' 카테고리의 다른 글
| [AWS] 20-3. AWS IAM Advanced, IAM Policy Evaluation Logic (0) | 2022.05.25 |
|---|---|
| [AWS] 20-2. AWS AD (Active Directory), Organizations, OU (0) | 2022.05.24 |
| AWS saml (0) | 2022.05.19 |
| [AWS] 19-6. AWS Config, Config Rules/Remediations/Notifications (0) | 2022.05.18 |
| [AWS] 19-5. CloudTrail (0) | 2022.05.16 |