What is Microsoft Active Directory (AD)?
사용자가 공유된 자원의 위치와 해당 서버의 로컬 사용자 계정을 모두 알고있지 않아도 중앙에서 Admin 이 사용자 인증 및 권한 부여 처리가 가능하도록 하여 기업내 자원 및 권한 관리에 사용.
Windows 환경에서 사용하기 위해 개발된 LDAP 디렉토리 서비스
- Found on any Windows Server with AD Domain Services
- Database of objects : User Accounts, Computers, Printers, File Shares, Security Groups
- Centralized security management, create account, assign permissions
- Objects are organized in trees
- A group of trees is a forest
* AD(Active Directory) : https://mpain.tistory.com/153
* LDAP : https://yongho1037.tistory.com/796
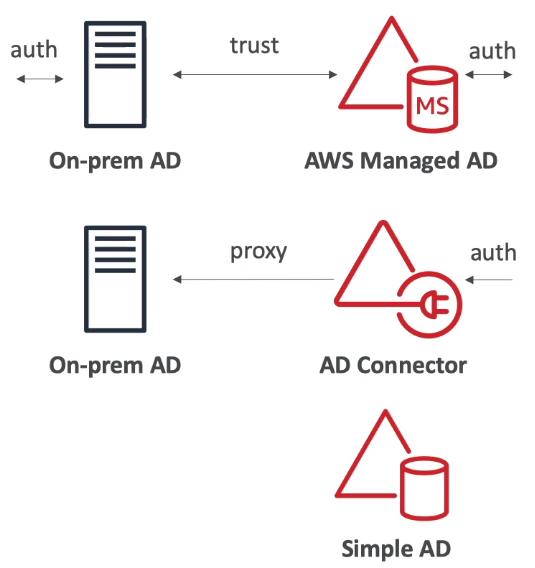
[ AWS Directory Services ]
- AWS Managed Microsoft AD
Create your own AD in AWS, managed users locally, supports MFA
Establish "trust" connections with your on-premise AD
- AD Connector
Directory Gateway (proxy) to redirect to on-premise AD, supports MFA
Users are managed on the on-premise AD
- Simple AD
AD-compatible managed directory on AWS
Cannot be joined with on-premise AD
[ AWS Organizations ]
- Global sevice
- Allows to manage multiple AWS accounts
- The main account is the master account - you cannot change it
- Other accounts are member accounts
- Member accounts can only be part of one organization
- Consolidated(병합된) Billing across all accounts - single payment method
- Pricing benefits from aggregated usage (volume discount for EC2, S3..)
- API is available to automate AWS account creation
[ Multi Account Strategies ]
- Create accounts per department, per cost center, per dev/test/prod, based on regulatory restrictions (using SCP), for better resource isolation (ex:VPC), to have separate per-account service limits, isolated account for logging
- Multi Account vs One Account Multi VPC
- Use tagging standards for billing purposes
- Enable CloudTrail on all accounts, send logs to central S3 account
- Send CloudWatch Logs to central logging account
- Establish Cross Account Roles for Admin purposes
[ Organizational Units (OU) - Examples ]

[ Service Control Policies (SCP) ]
IAM 작업에 대한 화이트/블랙 리스트
OU 혹은 계정에 적용
마스터 계정엔 적용되지 않음
ROOT 를 포함한 모든 계정 및 Role 에 적용
service-linked role 엔 적용되지 않음
SCP 는 명시적 허용이 있어야함 (default 는 모든 권한이 없음)
특정 서비스에 대한 액세스 제한 등 권한 제한용으로 사용 가능
- Whitelist or blacklist IAM actions
- Applied at the OU or Account level
- Does not apply to the Master Account
- SCP is applied to all the Users and Roles of the Account, including ROOT
- The SCP does not affect service-linked roles
Service-linked roles enable other AWS services to integrate with AWS Organizations and can't be restricted by SCPs
- SCP must have an explicit Allow (does not allow anything by default)
- Use cases :
Restrict access to certain services (for example : can't use EMR)
Enforce PCI compliance by explicitly disabling services
[ SCP - Hierarchy ]
하위 계층의 OU는 상위 계층의 OU 의 Access/Deny 정책을 따름
ex: Account B 는 Lambda와 Redshift 액세스 불가, Account A 는 Redshift 액세스 불가

[ AWS Organization - Moving Accounts ]
다른 organization 으로 계정 옮길 땐 asis organization 에서 계정 제거 후 tobe organization 에 초대 및 초대 수락하여 옮김
'infra & cloud > AWS' 카테고리의 다른 글
| [AWS] 20-4. Resource Access Manager (0) | 2022.05.26 |
|---|---|
| [AWS] 20-3. AWS IAM Advanced, IAM Policy Evaluation Logic (0) | 2022.05.25 |
| [AWS] 20-1. AWS STS, Identity Federation (0) | 2022.05.24 |
| AWS saml (0) | 2022.05.19 |
| [AWS] 19-6. AWS Config, Config Rules/Remediations/Notifications (0) | 2022.05.18 |